In the last post, we have discussed that it's very important to check potential security vulnerabilities in the 3rd party libraries/components we use while development. Today we would discuss, how to find security vulnerabilities in software components using OWASP Dependency Check maven plugin.
2. Scope
3. How to use OWASP Dependency Check utility
4. Action Plan for Security Vulnerabilities
5. Conclusion
In order to achieve overall application security, one need to also check the 3rd party software libraries/components whether these are free from any known, publicly disclosed, vulnerabilities.
Here, we would use OWASP Dependency Check utility to analyze all the external dependencies of our project and generate the vulnerability report. The tool is the solution to the OWASP Top 10 2013 A9 - Using Components with Known Vulnerabilities.
Some Important Pointers Regarding this Utility:
Here, we will only discuss about using OWASP Dependency Check utility as a Maven plugin.
Follow the below steps:
One need to make sure that project is not using any external libraries that is not safe to use. If one finds such external 3rd party libraries/components then please follow the below action plan:
Only writing secure code is not enough if vulnerable 3rd party libraries/components are used while development. If one uses OWASP Dependency Check utility as a Maven plugin then with every build one would know about any new vulnerabilities that are introduced after adding any new project dependencies. One could also make the dependency check report generation as a part of site generation process (all reports in one place 😊 )
Thank you for reading this article. Feel free to connect with me for any queries and suggestion. See you soon. Happy Learning !! 😉
Table Of Content
1. Introduction2. Scope
3. How to use OWASP Dependency Check utility
4. Action Plan for Security Vulnerabilities
5. Conclusion
1. Introduction
In order to achieve overall application security, one need to also check the 3rd party software libraries/components whether these are free from any known, publicly disclosed, vulnerabilities.
Here, we would use OWASP Dependency Check utility to analyze all the external dependencies of our project and generate the vulnerability report. The tool is the solution to the OWASP Top 10 2013 A9 - Using Components with Known Vulnerabilities.
Some Important Pointers Regarding this Utility:
- Currently only Java and .NET are supported; additional experimental support has been added for Ruby, Node.js, Python, and limited support for C/C++ build systems (autoconf and cmake).
- One can use this utility either as a command line interface, a Maven plugin, an Ant task, and a Jenkins plugin.
- It automatically updates itself using the National Vulnerability Database (NVD) Data Feeds hosted by NIST.
2. Scope
Here, we will only discuss about using OWASP Dependency Check utility as a Maven plugin.
3. How to use OWASP Dependency Check utility
Follow the below steps:
- Make the below entry inside the plugins section of POM file (pom.xml) for the required project
<build> ... <plugins> ... <plugin> <groupId>org.owasp</groupId> <artifactId>dependency-check-maven</artifactId> <version>2.1.1</version> <executions> <execution> <goals> <goal>check</goal> </goals> </execution> </executions> </plugin> ... </plugins> ... </build> - Build the Project using
mvn clean install
- Check the target directory, dependency check report (dependency-check-report.html) will be generated in this directory
Built the project after adding the required plugin entry and got the report. Just For Reference, adding some logs/screenshots: - Console log to show series of analyzers that inspect our project dependencies
[INFO] --- dependency-check-maven:2.1.1:check (default) @ pmd-demo --- [INFO] Checking for updates [INFO] Skipping NVD check since last check was within 4 hours. [INFO] Check for updates complete (18 ms) [INFO] Analysis Started [INFO] Finished Archive Analyzer (2 seconds) [INFO] Finished File Name Analyzer (0 seconds) [INFO] Finished Jar Analyzer (1 seconds) [INFO] Finished Central Analyzer (2 seconds) [INFO] Finished Dependency Merging Analyzer (0 seconds) [INFO] Finished Version Filter Analyzer (0 seconds) [INFO] Finished Hint Analyzer (0 seconds) [INFO] Created CPE Index (2 seconds) [INFO] Finished CPE Analyzer (2 seconds) [INFO] Finished False Positive Analyzer (0 seconds) [INFO] Finished Cpe Suppression Analyzer (0 seconds) [INFO] Finished NVD CVE Analyzer (0 seconds) [INFO] Finished Vulnerability Suppression Analyzer (0 seconds) [INFO] Finished Dependency Bundling Analyzer (0 seconds) [INFO] Analysis Complete (11 seconds) [WARNING] One or more dependencies were identified with known vulnerabilities in pmd-demo: validation-api-1.1.0.Final.jar (cpe:/a:bean_project:bean:7.x-1.1::~~~drupal~~, javax.validation:validation-api:1.1.0.Final) : CVE-2013-4499 tomcat-embed-core-8.5.20.jar (cpe:/a:apache:tomcat:8.5.20, cpe:/a:apache_software_foundation:tomcat:8.5.20, org.apache.tomcat.embed:tomcat-embed-core:8.5.20) : CVE-2017-12617 See the dependency-check report for more details. [INFO] ------------------------------------------------------------------------ [INFO] BUILD SUCCESS [INFO] ------------------------------------------------------------------------ [INFO] Total time: 26.728 s
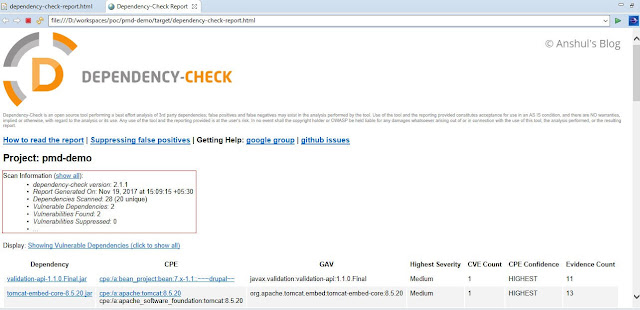
- Dependency Check Report Screenshot
- Terminologies used in report
CVE (Common Vulnerabilities and Exposures) - a unique identification number respective to known security vulnerability, in the format CVE-<reported year>-sequence number
CVSS (The Common Vulnerability Scoring System) - a score, a scale from 0 to 10, The severity is decided based on the CVSS score.
4. Action Plan for Security Vulnerabilities
One need to make sure that project is not using any external libraries that is not safe to use. If one finds such external 3rd party libraries/components then please follow the below action plan:
- When a known security vulnerability in a 3rd party library is identified then look for higher version of that library where the issue is fixed.
- If the latest version of a 3rd party library also have the known vulnerabilities, try using an alternative libraries which has no reported vulnerabilities.
- Situations where no option other than using a particular 3rd party library, but still that library has some known vulnerabilities then in such case, analyze each vulnerability and check if it has really any impact to our project or not.
5. Conclusion
Only writing secure code is not enough if vulnerable 3rd party libraries/components are used while development. If one uses OWASP Dependency Check utility as a Maven plugin then with every build one would know about any new vulnerabilities that are introduced after adding any new project dependencies. One could also make the dependency check report generation as a part of site generation process (all reports in one place 😊 )
Thank you for reading this article. Feel free to connect with me for any queries and suggestion. See you soon. Happy Learning !! 😉

No comments:
Post a Comment